NFS Misconfiguration
NFS stands for Network File System and it is a service that can be found in Unix systems.The purpose of NFS is to allow users to access shared directories in a network.However special effort needs to be done from system administrators in order to configure properly an NFS share.For the needs of this article we will use the Metasploitable 2 which by default has the NFS service misconfigured.
Lets say that we have scanned a system and we have discovered the NFS service running on port 2049 as we can see and from the image below:

Now we can use the command showmount -e IP in order to list the accessible shares of the remote system.
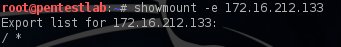
This means that the root directory of the remote system is shared!From the security perspective this can be catastrophic as any attacker can mount the whole directory and he can view the contents in a local directory as it can be seen in the next three following images:



As we can see we can view the folders of the root directory and we can of course obtain the contents of the /etc/passwd and /etc/shadow in order to have the user of the remote machine and the password hashes.


Conclusion
This article was just an example of how an NFS misconfiguration can exploited by a malicious attacker.Of course in nowadays it is difficult for a system administrator to perform these kind of mistakes but it is always good to know the commands and what to do in a situation like this especially when NFS is a subject in security related certifications.