In network infrastructure penetration tests if we manage to exploit one system then it is easy to obtain information for the network that this system is part of.This information is important because in almost every network penetration test the ultimate goal is to become domain administrator and in order to achieve that it is necessary to know the appropriate commands that will help us to gather information about the network that we are already inside.In this article we will see how we can gather information about windows networks that we are conducting the penetration test from the system that we have already exploited.
Lets say that we have exploited a windows system and we want to know more about the network that this system belongs to.The first and most common command is of course the ipconfig /all which it will display to us all the information about the network adapters of the host and the Windows IP configuration as the picture below is showing:

Another command is the ipconfig /displaydns which it will display the contents of local DNS cache.

Systems in internal networks most of the times contain shared folders which can be listed with the command net share.

We might also want to discover other internal networks that exist by examining the machine routing table with the command route print.

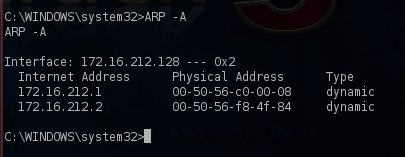
The ARP -A command will list all the systems that are currently in the machine’s ARP table helping us to discover other valid hosts.
We can also use the network diagnostic command of the system to obtain information about operating system,network adapters,network clients and other network configuration with the command netsh diag show all.

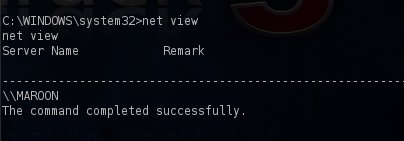
Another information that is important to learn about the host that we have exploited is to see which other hosts are on the same workgroup.The command that we will need to type is the net view.
Last but not least the netstat command can be used with the parameters -n -a -o to display all the active connections along with the IP addresses and process ID of each connection.

Conclusion
In this article we saw some common commands and their output that can be used for post exploitation activities in Windows networks.The majority of these commands will help us to identify new hosts and network shares which can lead us to compromise further systems on the network.
Reblogged this on Hacking and security and commented:
These are some of the basic and simple steps has to be taken after a successful penetration. Great post.
We can also code an exploit to automate all of these tasks, can save it in text files and something like those actions …
Nz
How about these tricks?
1. net use x: \\server\share “” /u:
2. net user username password /ADD /DOMAIN
3. net group “Domain Admins” username /ADD /DOMAIN
4. net user username password /ADD
5. net localgroup Administrators username /ADD
Thank you hackingtom for submitting these commands.I am planning to cover those and many more in another article about post exploitation. 😉
I would strongly disagree with this statement:
“This information is important because in almost every network penetration test the ultimate goal is to become domain administrator”
On the tests I do they are more usually target orientated, for example access a key piece of information, modify some data, demonstrate potential business impact of a compromise .I can’t really remember a job where a client has specifically set the goal of gaining domain admin.
It definitely helps with the rest of the job if you are DA but it shouldn’t really be the ultimate goal.
Maybe I didn’t express this correctly as I didn’t had either clients that they set this goal in meetings before the engagements.A pen test can be considered successful if the objectives that the client sets are met,right?However my view is that in infrastructure penetration tests if you have the chance to become Domain Admin you should take it.So from that point this can be the ultimate goal for penetration testers and we must almost try our possibilities to achieve this even if sometimes this it is not necessary or it can’t be achieved due to other parameters and restrictions.
I think if you can achieve your objectives without becoming DA then you shouldn’t do it. If the client sets you the goal of acquiring financial information and you find it on an open share on an accountants machine then you take it and it is game over. If the domain controller has ms08-067 on it then you wouldn’t pop a shell and add a DA account just to say you also got DA.
The ultimate goal is to meet the clients objectives, a lot of testers have a personal goal of getting DA as it makes them feel they have beaten the admin but that is different.